Introduction
While we often think of our government as a political institution that creates and enforces laws, policies, and regulations, it is at its core a recordkeeper, too. To govern its people, the government, as a centralized authority, relies on the creation and upkeep of trustworthy and retrievable records. Government and civilian decisionmaking will likely be critically impaired if the records we depend upon cannot be used or trusted. In short, good governance requires good recordkeeping.
Today, many of our vital records are digitally preserved in centralized databases. However, because centralized databases are single points of failure, our records are vulnerable to two types of dangers: technological and human dangers. Technological dangers are those that lead to records becoming irretrievable or unusable due to changes in technology or passage of time, and the destruction of data-storing hardware via natural disasters or human conflict. At bottom, technological dangers impact the longevity of records. Human dangers primarily involve data theft and malicious and non-malicious data manipulation. Data theft is the theft of sensitive records,1 typically for fraudulent purposes,2 and can greatly diminish the public’s trust in the government’s ability to protect their records. Data manipulation is the alteration or deletion of sensitive records, whether by a careless employee3 or malicious hacker,4 and can change public opinion, render critical information useless, and ultimately destroy trust in our own records.5
One proposed solution to address these recordkeeping concerns is blockchain technology. Proponents argue that blockchains are immutable and thus secure by design.6 In a blockchain network, every computer (node) in the system has a canonical copy of the network’s ledger. Once information is entered into a blockchain, it becomes extremely difficult to alter—thus making blockchains immutable. If a hacker or careless employee tries to unilaterally alter a ledger, she must create a new hash7 for the block being altered and every subsequent block in that ledger because every new block references the hashes of past blocks. This can require tremendous computational power. Additionally, even if she somehow did the above, she still needs all the other nodes to accept her unilateral changes. Unless she amasses most of the network’s computing power—known as a “51-percent attack”—her changes will be rejected. It is incredibly difficult to launch a 51-percent attack because it involves either compromising most of the nodes or acquiring enough hardware (for example, purchasing a lot of computers) to gain such computational power. With regard to ensuring the longevity of our records, even if every node goes offline, one node possessing the blockchain’s full history could revive the whole network by coming back online. Blockchain technology therefore holds enormous potential to protect our records from data manipulation and ensure their longevity.
The United States Citizenship and Immigration Services (USCIS) is a federal agency that administers the country’s immigration system and determines which immigrants are granted or denied certain immigration benefits. Like other federal agencies, the USCIS uses a centralized database8 to maintain the sensitive records of the public. Using a centralized database, however, means that those records are vulnerable to both human and technological recordkeeping dangers. To be unable to access one’s immigration records (such that an immigrant, for example, cannot prove their legal status) or to have the integrity of those records compromised can lead to deportation and being denied future admission into the United States.9 The USCIS, in short, could stand to benefit greatly from transitioning from a centralized system of records to a blockchain system, at least with regard to protecting our records from data manipulation and ensuring their longevity.
If the USCIS, or any federal agency, seeks to use blockchain technology as a solution to the above recordkeeping concerns, it must keep in mind that blockchain technology still has its limitations. First, depending on what type of blockchain is used, the government may not ultimately be in control of its blockchain.10 Simply put, control is the ability to govern a blockchain’s system processes and alter its records.11 There are three types of blockchains: open, mixed, and closed. Closed systems grant certain users control over the blockchain, open systems grant users no control, and mixed systems grant users varying levels of control. Significant problems will likely arise for both immigrants and the USCIS if the agency cannot correct erroneous or compromised records entered into its blockchain. Thus, if the government seeks control over its blockchain, it must use a closed system. Second, blockchains used in a government context cannot prevent data theft of original records. Finally, blockchains alone cannot ensure that records are reliable (that a record was created correctly) or authentic (that a record is what it says it is).12 As long as human error exists, there will be records created erroneously or otherwise left vulnerable to malicious actors before they are entered into a blockchain.
To be clear, I am not saying that the government should not use blockchain technology for recordkeeping purposes at all. Far from it, I am hopeful that the technology will likely improve in the years to come. At bottom, blockchain technology is an excellent, though imperfect, solution to the dangers of data manipulation and the destruction of hardware storing data via natural disasters or human conflict. Blockchain technology is not at all a catch-all solution for every recordkeeping problem. By taking note of what blockchain technology can and cannot do, the government can allocate its resources more efficiently and effectively to supplement blockchain technology’s shortcomings.
I. What Is a Blockchain?
Imagine you are a law student. When class begins, you and everyone in your section assigns themselves a seat for the semester. No physical seating chart is needed to keep track of who sits where since each student, including yourself, knows where everyone sits. You could say the same mental seating chart exists in everyone’s mind. Moreover, whenever someone changes seats, or tries to change seats, everyone notices and remembers this change.
Now imagine one day classmate T, for whatever reason, malicious or non-malicious, claims your seat is hers. For our purposes, there are two potential scenarios. Scenario one: T’s attempt to claim your seat as hers is noticed by everyone else and they will reject her attempt to unseat you because everyone knows that seat is yours and that T’s seat is elsewhere. Scenario two: T convinces at least 51 percent, the majority, of your classmates that your seat is hers—maybe the majority likes her more than you or she might have coerced them into changing their minds. Assume that no individual is more influential than anyone else. Whatever her approach, if the majority agree with T, and the minority say nothing about this change, then the class’s mental ledger will reflect this change by recording T as the rightful owner of the disputed seat.
In this hypothetical, you and your classmates are users who control computers, or nodes, in a blockchain. The seating chart represents a ledger that records every transaction that occurs in a blockchain and the seats represent anything of value, like land titles, for example. T represents a malicious or non-malicious actor (like a hacker or careless employee) who tries to alter the contents of a ledger. In a blockchain, one ledger is distributed across all the nodes, just as each student has a “mental ledger” of the seating.13 Whenever new transactions are added to the ledger, these transactions must be verified by all the nodes.14 Once new transactions are verified, each node will update its copy of the ledger accordingly so that, in theory, only one canonical version of the ledger exists at any time.15
A blockchain’s ledger is made up of blocks digitally chained together in chronological order of when each block was formed.16 Each block contains various data inputs, like claims to certain seats in a classroom, for example. Let us assume everyone in our hypothetical uses a blockchain to record who sits where. To claim a seat, you might input “Reader owns seat X” onto the blockchain. These informational inputs are not represented in plain English but rather as a string of letters and numbers of a fixed length called hashes.17 These hashes also contain references to the hashes stored in every past block.18 For example, block three’s hash will contain references to block two and one’s hashes just as block two’s hash will contain a reference to block one’s hash. Note that even the smallest change to the inputs of a hash (using lowercase “r” instead of uppercase “R” to spell “Reader,” for example) will result in a radically different hash.19 Thus, in blockchains where there exist tens or hundreds of thousand blocks,20 changing a block early in the system, and thus creating new hashes for every block thereafter, is almost impossible.
Returning to our hypothetical, scenario one is an example where an actor tries to unilaterally alter a blockchain’s ledger, without having compromised most of the system’s nodes. Since all the other nodes have a copy of the canonical ledger, they will all reject the unilateral changes made.21 Scenario two is where an actor has compromised 51 percent of the system’s nodes or, more accurately, its computational power. In our hypothetical, since everyone’s voice or computational power is equal, to compromise most of the system’s nodes is to therefore compromise most of the system’s computational power. This “51-percent attack,” as it is commonly known, could happen because a single entity has amassed such computational power (owning a lot of computers) or, as is more likely, a group of nodes have pooled their collective computational power.22
Reality is not as simple as our hypothetical, however, as one user may control many nodes and thus possess more computational power than others—akin to one of your classmates being more influential than others. However, being influential or controlling many nodes does not come easy. To possess most of the system’s computational power requires owning a lot of computers or allying oneself with other users to benefit from their nodes or take illicit control of other users’ nodes. In short, to mount a 51-percent attack requires considerable financial23 and even social capital, making a 51-percent attack incredibly difficult to accomplish.
If T tried to unilaterally change the contents of any block on the class blockchain, she must contend with two issues. First, T must possess enough computational power to create hashes for every block created after the altered block because the alteration of one block necessitates the creation of new hashes for all subsequent blocks. Second, even if she succeeded in creating new hashes for all subsequent blocks, she must possess most of the system’s computational power for her changes to be accepted. The existence of these two obstacles is what gives blockchains their trustworthy and immutable quality and thus makes blockchain technology an ideal solution against the growing threat of data manipulation.
II. Control
A. Characteristics of open, mixed, and closed blockchains
Blockchains can be divided into three categories on a spectrum: open, mixed, and closed.24 Before exploring these three categories, a brief introduction of “consensus algorithms,” “cryptocurrencies,” and “reading and writing privileges” is necessary. A blockchain’s consensus algorithm determines how blocks are processed and added to the system’s ledger.25 To return to our classroom hypothetical, consensus algorithms would be the means by which the class comes to an agreement as to who sits where. Most consensus algorithms, put simply, create cryptographic (math) problems of varying difficulty levels, that users who verify transactions must solve (by finding the correct hash) in order to process blocks.26 The type of consensus algorithm used by a system influences whether users place their trust in the system or each other. Cryptocurrencies are offered to users as an incentive to continue verifying transactions and playing by the rules, since in many blockchains users do not know nor trust other users. Not all blockchains offer users cryptocurrencies or require users to solve math problems to verify transactions.27 Finally, different blockchains offer varying types of reading and writing privileges to its users.28 Reading privilege is the extent to which a user is able to freely read or query data from a blockchain. Writing privilege is the extent to which a user is able to freely create new entries and verify entries created by her or others.
Open blockchains, on one end of the spectrum, are accessible to anyone with an internet-connected device and free software that is compatible with the respective blockchain’s network.29 Users do not need to be identified in the real world to participate in open blockchains and can use the system pseudonymously.30 All nodes can read and write transactions onto the ledgers.31 But, since there is no central enforcer of rules, users must rely on strangers to honestly create and verify transactions. Moreover, users must be incentivized to verify the transactions of others because open blockchain consensus algorithms are typically extremely difficult and expensive to solve.32
These math problems were designed to be exceedingly complex primarily to make it costly for users to verify transactions because users who have invested considerable stake in the system will be less likely to sabotage the system’s integrity for their own benefit.33 Unless a majority of the users agree to change a portion of the ledger, open blockchain ledgers are immutable. The combination of immutability and having a stake in the system, in order to verify transactions, fosters a trustless system where users do not need to have trust in other users for the system to work because users place their trust in the system itself.
Closed blockchains, on the other end of the spectrum, are managed by a few controlling users who have full reading and writing privileges.34 Non-controlling users must be identified offline by the controlling users in order to use the blockchain and have access only to partial nodes with permission either to read or to write.35 Controlling users ensure everyone plays by the rules. Since closed blockchains are normally operated by institutions, like a bank or government agency, controlling users may be organization personnel. Closed blockchains do not typically use complex math problems for the verification process or offer its users cryptocurrencies36 because the controlling users, who are responsible for verifying transactions, are self-incentivized37 to verify transactions.
Since the number of controlling users in a closed blockchain is limited, these parties may more readily come to an agreement—at least with respect to an agreed upon organization agenda—than nodes in an open or mixed blockchain to change aspects of the ledger when necessary. The centralized nature of a closed blockchain means that this system is not immutable. That is, a blockchain is not immutable if changes can easily be made, say, after a few members have a talk in a meeting. An open blockchain is immutable because it is so difficult to get so many users to agree upon one viewpoint. A closed blockchain is pseudo-immutable, however, in that a malicious actor must still compromise 51 percent of the nodes to manipulate the ledger. Keep in mind that controlling users are typically institutions like banks or government agencies. So, while they may be few in numbers, each controlling user may have thousands or more full nodes under their control. In short, users place their trust in each other, or more precisely the controlling users, rather than the system.
Mixed blockchains, as illustrated in Figure 1, can be open for reading and closed for writing, or closed for reading and open for writing.38 Users may or may not be required to identify themselves in the real world before participating. These blockchains can utilize different types of consensus mechanisms and may or may not use cryptocurrencies to incentivize its users to verify transactions. In short, mixed blockchains share characteristics of both open and closed blockchains to varying degrees.39
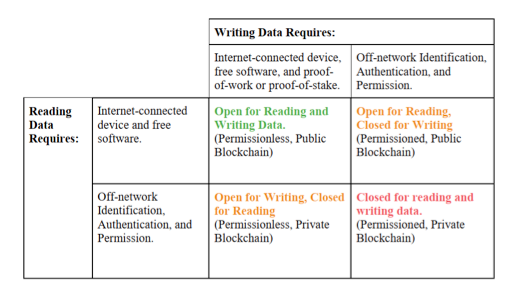
Figure 140
B. How Much Control Does the Government Need Over Its Blockchain? What Type of Blockchain Is Best for the Job?
If the government seeks to use blockchain technology as a means of preventing digitally stored public records from being stolen and manipulated, and increasing the longevity of our records, it should first determine how much control it needs over its blockchain. I define “control” as the ability to decide who can read and write data onto a blockchain’s ledger, alter portions or the entirety of its ledger, and stop or start its operations (that is, pausing the whole blockchain so that no new entries can be added onto its ledger). The more control the government needs, the more centralized the blockchain must be. Closed blockchains thus provide the most control, while open blockchains provide the least.
Regardless of which government agency is using a blockchain for recordkeeping purposes, if the respective agency cannot afford to make immutable mistakes because the scale of harm41 to the public would be too great, then the only type of blockchain it should use is a closed blockchain. The types of government agencies that best fit this description are those that provide benefits directly to the public on a large scale. A closed blockchain, rather than an open one, is especially appropriate where it is crucial to the individuals applying for benefits (applicants) that they can appeal decisions.
The USCIS is one such agency that directly provides benefits to the public. Applicants are immigrants seeking immigration benefits where the consequences of applying for such benefits can often mean remaining lawfully in the United States or getting deported. To the extent that the law allows, applicants must have some means of appealing an adverse decision if they wish to remain in the United States.
If the USCIS used an open blockchain, the USCIS would not be able to erase the adverse decision even if the immigrant’s judicial appeal was successful because the ledger is immutable. The USCIS would only be able to create a new entry that states what the immigrant’s correct immigration status is. On a case-by-case basis, this is not necessarily an ill-advised approach, provided the USCIS has the resources to correct incorrect entries in a timely fashion.
The reality, however, is that the USCIS has been backlogged for many years, with no end to the various backlogs in sight.42 It therefore seems unlikely that the USCIS would be able to correct entries on a case-by-case basis in a timely fashion. Moreover, if the USCIS needed to correct a large number of entries erroneously entered due to some technical or systemic human error, an open blockchain would not allow the USCIS to do this (barring the USCIS compromising 51 percent of the nodes—recall that a 51-percent attack is very difficult to do). Finally, if the USCIS needed to halt the creation of all new entries, an open blockchain would also not allow it to do this; only a closed blockchain would. A closed blockchain is thus the answer to all the above problems since it would allow the USCIS to rewrite specific entries or large sections of the ledger, or otherwise pause the blockchain while it figures out a solution to some systemwide technical error.
III. Blockchains Used in a Government Context Cannot Prevent Data Theft of Original Records
If the government must have access to an applicant’s original records43 to provide her with the benefits she seeks, the government cannot use blockchain technology to prevent the theft of her original records. Blockchains cannot currently store original records on its system, and original records cannot be reproduced from hashes of records stored on a blockchain.44 While users can include certain sensitive information in a blockchain entry, like one’s social security number or address, this is not the same as saying that the original records from where the sensitive information is derived can be stored on a blockchain.45
To put the above into context, when the USCIS, for example, adjudicates an adjustment of status case for an immigrant married to a U.S. citizen or legal permanent resident (LPR) to become an LPR, the immigrant and her sponsoring spouse must submit proof of their bona fide marriage to the USCIS.46 This proof includes copies of various original records that the couple would not want in the hands of a malicious actor. However, since the USCIS cannot store all these original records in the blockchain, the USCIS must therefore store them in a centralized database. But to store the couple’s original records in a centralized database is to expose those records to data theft because all centralized databases inevitably have single points of failure. In this particular governmental context, a blockchain cannot protect data theft of original records.
Additionally, the public’s sensitive information can be accessed if malicious actors gain access to the private keys linked to blockchain entries that contain sensitive information. Briefly explained, blockchain users have private keys that are used to sign a transaction so that the intended party knows that the transaction was created by that user. This private key is somewhat analogous to login credentials: Without your key, you cannot “login” to your blockchain account. Because private keys are commonly stored on a node’s local storage,47 these keys are only as safe as the node’s security. In other words, a user’s node is another centralized single point of failure.
Finally, if a public user loses her private key does this mean that she has no recourse to access her public records stored on the government’s blockchain? Not necessarily. On one hand, the USCIS, for example, could maintain a copy of applicants’ private keys in case applicants lose theirs. But again, a familiar problem arises: The government must necessarily store these private keys in a centralized database, yet another single point of failure ripe for a hacker to breach. On the other hand, the USCIS could choose not to store applicants’ private keys. This will very likely create due process issues if certain immigrants are rendered deportable because they cannot prove their immigrant status, or appeal their wrongly adjudicated immigration status, by presenting the evidence of their public records stored on the government’s blockchain.
IV. Trustworthiness
Whether a record is trustworthy or not depends on two concepts: reliability and authenticity. Reliability asks if a record is an accurate statement of fact.48 Authenticity, on the other hand, asks if a record is an accurate record, “that the record is what it purports to be, free from corruption or tampering.”49
Blockchains cannot guarantee the reliability of records because a record’s reliability depends on “the competence of its author, its completeness, and the controls on its creation.”50 For example, if senior USCIS officials were to inadvertently issue a directive to its employees to adjudicate certain cases in a mistaken way, this compromises any records made under compliance with the directive. Other ways the reliability of records can be compromised include the incompetent efforts of workers and applicants, and the lack of quality-check mechanisms in place to prevent mistakes from being made.
Blockchain technology is an attractive solution to recordkeeping problems because it is supposedly able to ensure the authenticity of records. This is true to an extent: A blockchain can only ensure the authenticity of the record that was entered into its ledger. Assume the USCIS has accurately adjudicated an applicant’s case and will transmit the adjudication information onto its blockchain. As the node transmits this information onto the blockchain, there is a possibility for a Man-in-the-Middle Attack (MitMA). “MitMA occurs when an attacker secretly intercepts and possibly alters the communication between two parties . . . directly communicating with each other.”51 A hacker could intercept the transmitted record and replace it with an invalid one.52 The invalid record entered into the blockchain would be subject to all the protections the blockchain offers. Thus, the record’s authenticity is compromised.53 Other ways a hacker could compromise transactions include Denial-of-Service attacks, Sybil attacks, and timing errors.54
That blockchain technology can neither completely ensure the reliability nor authenticity of records does not necessarily damage its overall appeal as a solution to data manipulation and record longevity issues. Blockchain technology is not meant to be a catch-all panacea for every recordkeeping problem. It is highly unlikely that any technology can ensure the reliability of records because there will always be human error and thus this is not a problem that concerns blockchain technology exclusively. Whether blockchains can ensure the authenticity of records depends largely on the state of cybersecurity technology. Regardless, it is the combination of blockchain technology’s immutable and distributed ledger characteristics that make it the best solution thus far to data manipulation and increasing record longevity.
Conclusion
Blockchain technology is an imperfect but excellent means of countering the threat of data manipulation and increasing the longevity of our records. Blockchains cannot ensure the trustworthiness of records, it cannot prevent data theft, and, if an open blockchain were used, the government would not have control over its blockchain.
None of this is to suggest that the government should not pursue a blockchain solution to its recordkeeping concerns. Perhaps in the future, original records might be stored entirely on a blockchain, thus creating a path for blockchains to protect our sensitive records from data theft by reducing the government’s need of storing such records in a centralized database; biometric data may one day replace private keys so that, in theory, we can never lose our keys; or, the government may develop a means of adjudicating benefits cases without need for our original records.
In the meantime, if the government is thinking about using blockchains for recordkeeping purposes, it should take note that, given the current state of technology, it must accept that centralized databases will continue to be necessary and used alongside blockchains to store things like private keys and original records. Blockchain technology is revolutionary in many ways—but it cannot do everything.
1 Think: social security numbers, addresses, passwords, and so on.
2 A prime example of data theft is the 2017 Equifax breach that resulted in 143 million people’s private data being stolen. Tara Siegel Bernard et al., Equifax Says Cyberattack May Have Affected 143 Million in the U.S., N.Y. Times (Sept. 7, 2017), https://www.nytimes.com/2017/09/07/business/equifax-cyberattack.html.
3 See TC Currie, GitLab Data Loss Incident Prompts a Review of Its Restore Processes, New Stack (Feb. 3, 2017, 7:52 AM), https://thenewstack.io/minimal-data-loss-gitlab-leads-major-review-restore-processes (discussing a GitLab employee’s accidental deletion of valuable company data).
4 In 2015, the Director of National Intelligence identified data manipulation as a potential cyber threat to U.S. national and economic security. James R. Clapper, Dir. of Nat’l Intelligence, Statement for the Record, Worldwide Cyber Threats, House Permanent Select Committee on Intelligence 5 (2015); see also U.S. Senate Select Comm. on Intelligence, Russian Targeting of Election Infrastructure During the 2016 Election: Summary of Initial Findings and Recommendations (2018) (discussing the U.S. Senate Intelligence Committee’s conclusion that cyber actors affiliated with the Russian government had penetrated certain voter registration databases and, at a minimum, were able to alter or delete voter registration data).
5 Ramona Carr, Data Integrity Attacks: Is Data Manipulation More Dangerous Than Theft?, Zettaset (Feb. 13, 2018), https://www.zettaset.com/blog/data-integrity-attacks-data-manipulation-more-dangerous/.
6 See generally Nir Kshetri, Blockchain’s Roles in Strengthening Cybersecurity and Protecting Privacy, 41 Telecomm. Pol’y 1027 (2017); Richard Kestenbaum, Why Bitcoin Is Important for Your Business, Forbes (Mar. 14, 2017, 9:22 AM), https://www.forbes.com/sites/richardkestenbaum/2017/03/14/why-bitcoin-is-important-for-your-business/#15d93c341b51.
7 For now, think of a hash as a long string of letters and numbers that represent the information stored in blockchains. See infra Section II for a deeper explanation of what hashes are.
8 The USCIS uses a centralized cloud system. See DHS/USCIS/PIA-009 Central Index System, Dep’t of Homeland Security (Dec. 17, 2018), https://www.dhs.gov/publication/dhsuscispia-009-central-index-system; Amanda Ziadeh, Thanks to Cloud and Encryption, USCIS Data Stays Secure, GovernmentCIO Media (June 1, 2018, 11: 26 AM), https://governmentciomedia.com/thanks-cloud-and-encryption-uscis-data-stays-secure.
9 See generally 8 U.S.C.A § 1182 (2013); 8 U.S.C.A § 1227 (2013).
10 Victoria L. Lemieux, Trusting Records: Is Blockchain Technology the Answer?, 26 Rec. Mgmt. J. 110, 124–25 (2016).
11 See infra Section III.B where I define control more comprehensively.
12 Lemieux, supra note 10, at 125–29.
13 See generally Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System (2008), https://bitcoin.org/bitcoin.pdf.
14 Id.
15 Id.
16 Id.
17 See generally What Is Hashing? Under the Hood of Blockchain, Blockgeeks, https://blockgeeks.com/guides/what-is-hashing/.
18 Id.
19 Id.
20 As of my writing this piece, the Bitcoin blockchain contained 557,260 blocks.
21 Nakamoto, supra note 13.
22 While my explanation of the 51 percent attack concept captures the gist of it, it is not technically complete. For a more thorough and technical discussion of the concept, see Jimi S., Blockchain: How a 51% Attack Works (Double Spend Attack), Medium (May 5, 2018), https://medium.com/coinmonks/what-is-a-51-attack-or-double-spend-attack-aa108db63474.
23 As of November 29, 2018, it would have cost a user $1.4 billion and electricity to power Morocco for a year in order to launch a 51 percent attack on the Bitcoin blockchain. See Mitchell Moos, Analysis: Bitcoin Costs $1.4 Billion to 51% Attack, Consumes as Much Electricity as Morocco, CryptoSlate (Nov. 29, 2018), https://cryptoslate.com/analysis-bitcoin-costs-1-4-billion-to-51-attack-consumes-as-much-electricity-as-morocco/.
24 See generally Peter Van Valkenburgh, Open Matters: Why Permissionless Blockchains Are Essential to the Future of the Internet 24–25 (2016). Note that Van Valkenburgh does not actually use the term “mixed” to describe a particular type of blockchain. I use the term “mixed” to describe blockchains with characteristics of both open and closed blockchains.
25 See generally CoinBundle Team, Consensus Algorithms, Securing Blockchain Transactions, Medium (Sept. 21, 2018), https://medium.com/coinbundle/consensus-algorithms-dfa4f355259d.
26 Id.
27 Van Valkenburgh, supra note 24, at 22.
[28] Id. at 24–25.
[29] Id.
[30] Id.
[31] Id.
[32] Id.
[33] See id. at 17–20 for a more nuanced discussion of the purpose of these complex math problems.
[34] Id. at 24–25.
[35] Id.
[36] Id.
[37] The self-incentivization often stems from the fact that institutions that use closed blockchains typically do so because they want to reap the benefits of blockchain technology while maintaining control over it. See Robert Brinkman, Choose Your Blockchain Consortium and Know Your Peers, Blockchain Pulse: IBM Blockchain Blog (Jan. 5, 2018), https://www.ibm.com/blogs/blockchain/2018/01/choose-your-blockchain-consortium-and-know-your-peers/.
[38] Van Valkenburgh, supra note 24, at 25.
[39] Id.
[40] Id. This chart comes directly from the source.
[41] I use the term “harm” broadly to include legal, institutional, economic, and social harms suffered by the general public and individuals.
[42] See Migration Policy Institute, Behind the Naturalization Backlog: Causes, Context, and Concerns 1 (2008) (stating that nearly one million cases were pending by December 2007); Daniella Silva, Citizenship Application Backlog 'Skyrocketed' to Near 730,000 Under Trump, Report Finds, NBC News (July 2, 2018, 8:00 AM), https://www.nbcnews.com/news/latino/citizenship-application-backlog-skyrocketed-under-trump-report-finds-n888146 (stating that the 388,832 naturalization case backlog under Obama as of December 2015 increased to roughly 730,000 pending cases under Trump as of December 2017); see also USCIS, Affirmative Asylum Statistics June 2018 (2018) (showing roughly 320,000 asylum cases were backlogged as of June 2018), https://www.uscis.gov/sites/default/files/USCIS/Outreach/Upcoming%20National%20Engagements/AffirmativeAsylumStats_June2018.pdf; S. Megan Berthold & Jane McPherson, Commentary: Fractured Families: US Asylum Backlog Divides Parents and Children Worldwide, J. Hum. Rts. Soc. Work 78, 78 (2016) (stating that 82,175 cases were backlogged as of March 2015).
[43] Paper or digital copies of records identifying who the applicants are or what they have done, such as birth certificates, passports, immigration visas, social security cards, tax documents, and land titles.
[44] Lemieux, supra note 10, at 119.
[45] Id.
[46] See generally 8 U.S.C.A § 1255(e) (2009).
[47] Lemieux, supra note 10, at 126.
[48] Luciana Duranti & Corrine Rogers, Trust in Digital Records: An Increasingly Cloudy Legal Area, 28 Computer L. & Security Rev. 522, 525 (2012).
[49] Id.
[50] Id.
[51] Lemieux, supra note 10, at 125.
[52] Id.
[53] While a Man-in-the-Middle Attack (MitMA) attack may be effective when a few records are being manipulated, it is hard to imagine how such an attack would succeed when it involves a large number of records. It is one thing to steal data, it is quite another to substantially compromise a record’s integrity without anyone noticing. Large scale data manipulation of this sort is almost akin to producing nearly flawless forgeries of difficult artworks, but on a large scale.
[54] See Lemieux, supra note 10, at 125, for a thorough discussion of what these attacks look like. But see Kshetri, supra note 6, at 1036 (arguing that as cryptographic security advances, “most of the current hacking activities can be eliminated or at least reduced”).
